Table of contents
In the previous blog, Getting Started with AWS Basics I explained AWS, its global infrastructure, and services offered by AWS that are useful for a DevOps engineer. In this blog let’s switch to a bit of automation part.🛠
User Data in AWS
![]()
What is User Data?
AWS User Data is the set of commands/data you can provide to a instance at launch time.
In other words, When you create an instance, in Amazon EC2 (Elastic Compute Cloud), you can provide some extra information to the instance. This additional information is known as user Data, and it helps you automate certain setup tasks or run scripts on the instance after it starts.
You can also pass this data into the launch instance wizard as plain text, as a file (this is useful for launching instances using the command line tools), or as base64-encoded text (for API calls).
User data can be passed to Amazon EC2 in two formats: -
Shell scripts: Shell scripts are a series of commands or instructions that can be executed by the instance’s operating system.Cloud-init directives: Cloud-init is a widely used system for configuring instances in the cloud. It supports a broader range of configuration options compared to shell scripts. With cloud-init, you can provide a set of directives that specify how the instance should be configured.
Why User Data?
Using User Data to launch your web server in Amazon EC2 (Elastic Compute Cloud) has its own pros👍 and cons👎.
PROS👍: -
Automation: User data allows you to automate the configuration of your EC2 instances during the launch process. This can include tasks such as installing software, configuring settings, and running scripts, saving time and effort.Customization: You can customize the setup of your EC2 instances based on your specific requirements, ensuring that they are tailored to your needs from the moment they are launched.Consistency: By using user data, you can ensure that all your EC2 instances are consistently configured, reducing the risk of configuration errors.
CONS👎: -
Complexity: Writing and managing user data scripts can add complexity to your infrastructure management, especially as your system grows and evolves.Maintenance: User data scripts need to be maintained and updated as your requirements change, which can add an additional layer of management overhead.Security: Improperly managed user data scripts can potentially introduce security vulnerabilities if they are not carefully designed and tested.
Identity and Access Management(IAM)

What is Identity?
Identity in a computing context means a certain set of properties that can be conveniently measured and recorded digitally.
The three most widely used authentication factors are:
Something the user knows: This factor is a piece of knowledge that only one user should have, like a username and password combination.Something the user has: This factor refers to possession of a physical token that is issued to authorized users, like a key fob, a USB device, or even a smartphone.Something the user is: This refers to a physical property of one's body, like Face ID, Fingerprint.
What is Access Management?
Access refers to what data a user can see and what actions they can perform once they log in.
Access management is the process of controlling and tracking access. Each user within a system will have different privileges within that system based on their individual needs.
What is IAM?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can centrally manage permissions that control which AWS resources users can access.
IAM for short, is a way to tell who a user is and what they are allowed to do.
With IAM you can create groups and allow those users or groups to access some servers, or you can deny them access to the service.
How does IAM Works?
The IAM workflow includes the following six elements:
Principal: is an entity that can perform actions on an AWS resource. A user, a role or an application can be a principal.Authentication: is the process of confirming the identity of the principal trying to access an AWS product. The principal must provide its credentials or required keys for authentication.Request: A principal sends a request to AWS specifying the action and which resource should perform it.Authorization: By default, all resources are denied. IAM authorizes a request only if all parts of the request are allowed by a matching policy. After authenticating and authorizing the request, AWS approves the action.Actions: are used to view, create, edit or delete a resource.Resources: A set of actions can be performed on a resource related to your AWS account.
Features of IAM
Here are some of the main features of IAM: -
Shared access to the AWS account: The main feature of IAM is that it allows you to create separate usernames and passwords for individual users or resources and delegate access.Granular permissions: Restrictions can be applied to requests. For example, you can allow the user to download information, but deny the user the ability to update information through the policies.Multifactor authentication(MFA): IAM supports MFA, in which users provide their username and password plus a one-time password from their phone—a randomly generated number used as an additional authentication factor.Password policy: The IAM password policy allows you to reset a password or rotate passwords remotely. You can also set rules, such as how a user should pick a password or how many attempts a user may make to provide a password before being denied access.Free to use: There is no additional charge for IAM security. There is no additional charge for creating additional users, groups or policies.Identity Federation: If the user is already authenticated, such as through a Facebook or Google account, IAM can be made to trust that authentication method and then allow access based on it. This can also be used to allow users to maintain just one password for both on-premises and cloud environment work.
Accessing IAM
You can work with AWS IAM in any of the following ways: -
AWS Management Console: The console is a browser-based interface to manage IAM and AWS resources. For more information about accessing IAM through the console
AWS Command Line Tools: You can use the AWS command line tools to issue commands at your system's command line to perform IAM and AWS tasks. Using the command line can be faster and more convenient than the console
Components of IAM
There are mainly 4 components of IAM. They are: -
Authentication: This process actively verifies the identity of employees or users by requesting their unique identifiers and necessary credentials to prove the authenticity of each user. This can include usernames, emails, passwords, biometric features like fingerprint or facial recognition, and electronic access like swipe cards, smartcards, etc. The process of authentication is often referred to as AuthN.Authorization: By default, all resources are denied. IAM authorizes a request only if all parts of the request are allowed by a matching policy. After authenticating and authorizing the request, AWS approves the action. It is commonly referred to as AuthZ.Administration: This component of the IAM system manages users accounts, groups, permissions, and password policies. It monitors the creation and modification of users accounts. For security reasons, it ensures that accounts use strong passwords and prompts users to change their passwords before a successful attack is launched.Auditing and Reporting: This component deals with examining, recording, and adequately reporting users access logs and all security-related activities within the system. This keeps the system safe and supports further compliance with necessary regulations guiding the business. Depending on the industry, there are different rules and regulations to follow, with many mandating continuous auditing and reporting just to protect users data. This includes regulations such as CPRA, HIPAA, PCI DSS, GDPR, etc.
IAM Identities
Below are the IAM Identities: -
Users
Groups
Policies
Roles
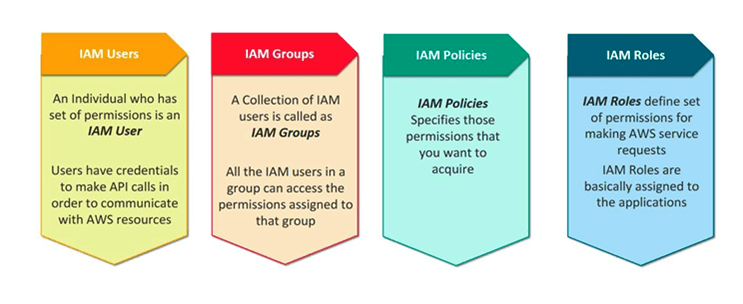
Let's Deep dive into all of these IAM identities.
IAM Users
An IAM user is an identity with an associated credential and permissions attached to it. This could be an actual person who is a user, or it could be an application that is a user.
With IAM, you can securely manage access to AWS services by creating an IAM username.
Each IAM user is associated with only one AWS account. By default, a newly created user is not authorized to perform any action in AWS.
The advantage of having one-to-one user specification is that you can individually assign permissions to each user.
IAM Groups
A collection of IAM users is an IAM group. You can use IAM groups to specify permissions for multiple users so that any permissions applied to the group are applied to the individual users in that group as well.
Managing groups is quite easy. You set permissions for the group, and those permissions are automatically applied to all the users in the group. If you add another user to the group, the new user will automatically inherit all the policies and the permissions already assigned to that group.
IAM Policies
An IAM policy sets permission and controls access to AWS resources. Policies are stored in AWS as JSON documents. Permissions specify who has access to the resources and what actions they can perform.
The policy would contain the following information:
Who can access it
What actions that user can take
Which AWS resources that user can access
When they can be accessed
There are two types of policies: -
Managed Policy: is a default policy that you attach to multiple entities (users, groups, and roles) in your AWS account. Managed policies, whether they are AWS-managed or customer-managed, are stand-alone identity-based policies attached to multiple users and/or groups.Inline Policies: are policies that you create that are embedded directly into a single entity (user, group or role).
IAM Roles
An IAM role is a set of permissions that define what actions are allowed and denied by an entity in the AWS console. It is similar to a user in that it can be accessed by any type of entity (an individual or AWS service).
Role permissions are temporary credentials.
Different types of IAM Roles: -
Service Role: AWS services are the trusted entity type for these roles, which are created to allow AWS services to perform actions on the user’s behalf.Service-linked Role: A service-linked role is a unique kind of IAM role linked to an AWS service. It simplifies the process of setting up a service by automatically adding all the required permissions for a service to perform actions on the user’s behalf. It is predefined by the service. Most service-linked roles do not permit changes to trust or permission policies.Web Identity role: A user assumes a web identity role when they log in to AWS using an identity provider(IdP) such as Amazon and Facebook. Users do not have an identity within AWS itself; in exchange for an authentication token, they get temporary security credentials in AWS that map to an IAM role that is authorized to use the resources in the AWS account.SAML 2.0 federation role: These roles are assumed by users who are included in an external user directory, typically within organizations. This enables federated single sign-on (SSO), so that organizations can give users access to the AWS console and CLI without having to create a separate IAM user for each person.Custom IAM role: Custom roles allow us to define exact permissions.
In the previous blog, we have seen how to create a user. Refer: Create an IAM User.
Add User Data and Create Roles
In this, we will launch the EC2 instance with already installed Jenkins on it. Once the server shows up in the console, hit the IP address in the browser and your Jenkins page should be visible.
Step 1: Login to AWS Console and Search EC2 and launch an instance.
Step 2: Given the below details for the creation of instance:
Name of the instance: userdata-server
Application and OS Images (Amazon Machine Image): Ubuntu
Instance Type: t2.micro
Key Pair: Select the key pair you have generated or create a new key pair.
Network settings: Check the boxes for “Allow HTTPS traffic from the Internet” and “Allow HTTP traffic from the Internet”



Step 3: Now expand the Advanced Details tab.

Step 4: Scroll down to User Data — optional box.

Step 5: In the box, enter the script that we need to be executed.
#!/bin/bash
sudo apt-get update -y
sudo apt install openjdk-11-jre -y
curl -fsSL https://pkg.jenkins.io/debian-stable/jenkins.io-2023.key | sudo tee \
/usr/share/keyrings/jenkins-keyring.asc > /dev/null
echo deb [signed-by=/usr/share/keyrings/jenkins-keyring.asc] \
https://pkg.jenkins.io/debian-stable binary/ | sudo tee \
/etc/apt/sources.list.d/jenkins.list > /dev/null
sudo apt-get update
sudo apt-get install jenkins -y
sudo systemctl enable jenkins
sudo systemctl start jenkins

Step 6: Now, Click on Launch Instance.

Step 7: Make sure you open port 8080 in the inbound rules of security group to the instance.


Step 8: Now, In the browser open the Jenkins UI using the <Public_IP:8080>.
We will get the Jenkins page if the script we passed as User Data was executed successfully.

Step 9: Now, Go to AWS Management Console > IAM > Roles.

Step 10: Click on Create Role.

Step 11: In Select trusted entity, Select AWS Service. Common Use Cases as EC2.

Step 12: Click on Next.
Step 13: In Add permissions, Give full access to EC2 creation and management.

Step 14: Click on Next.
Step 15: In Name, review, and create.
In Role name: DevOps-user


Step 16: Review the details and Click on Create Role.
Step 17: Role has been create successfully.

Conclusion
In Conclusion, AWS User data is the set of commands/data you can provide to a instance at launch time.
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources.
We looked into different Components of IAM are Authentication, Authorization, Administration and Auditing & Reporting.
Also, we looked into different IAM Identities are: -
Usersrepresent individuals with AWS accounts.Groupsstreamline permission assignments.Policiesset access controls.IAM Rolesdefine permissions for temporary access.
Also, In this blog we have added user data in EC2 instance and created Roles in AWS.
Hope you find it helpful🤞 So I encourage you to try this on your own and let me know in the comment section👇 about your learning experience.✨
*👆The information presented above is based on my interpretation. Suggestions are always welcome.*😊
~Smriti Sharma✌